NIST 800-53 for Product Security: Making Compliance Work for Engineers, Not Against Them

When I first encountered NIST 800-53, my immediate reaction was somewhere between confusion and mild panic. Here was this massive framework with over 1,000 controls that seemed designed more for compliance officers than for the engineers actually building products. But here's what I've learned after years of wrestling with these controls: when implemented thoughtfully, NIST 800-53 doesn't have to be the enemy of fast-moving development teams. In fact, it can become your secret weapon.
Gone are the days when product security meant running a vulnerability scanner before launch and crossing your fingers. Today's security leaders get it, real protection comes from weaving security into every stage of development. And surprisingly, that's exactly what NIST 800-53 has been trying to tell us all along.
Table of Contents
- Why NIST 800-53 Actually Makes Sense for Product Teams
- The Controls That Actually Matter for Product Development
- The Real Implementation Challenges (And How to Solve Them)
- Continuous Compliance vs. Point-in-Time Audits
- Security Architecture Reviews at Development Speed
- Evidence Generation for Multiple Stakeholders
- Making NIST 800-53 Work in Practice
- The Role of Modern Security Review Platforms
Why NIST 800-53 Actually Makes Sense for Product Teams
.png)
NIST Special Publication 800-53, officially titled Security and Privacy Controls for Information Systems and Organizations, started life as a framework for federal systems. But don't let that government pedigree fool you. What the folks at NIST created was something much more valuable: a comprehensive playbook for building security into products from the ground up.
The framework organizes its controls into 20 families, covering everything from access control to system integrity. But if you're a product security manager trying to figure out where to start, let me save you some time. Three control families should be at the top of your list: System and Services Acquisition (SA), Risk Assessment (RA), and Configuration Management (CM). These are the controls that directly impact how you build, deploy, and maintain your products.
What sets NIST 800-53 apart from other frameworks is its emphasis on "security by design." Instead of treating security as something you bolt on later, it pushes you to bake protection into your architecture from day one. Sound familiar? That's because it aligns perfectly with the shift-left methodology that smart development teams have been adopting for years.
.png)
The Controls That Actually Matter for Product Development
SA-8: Security and Privacy Engineering Principles
If there's one control that product security teams need to master, it's SA-8. It’s all about fundamentally changing how you approach system design.
Here's what SA-8 actually requires:
- Security-first architecture: Your design decisions need to consider security implications from the start
- Integrated development lifecycle: Security can't be an afterthought in your SDLC
- Systematic threat modeling: You need processes to identify and mitigate attack vectors
- Developer enablement: Your team needs the training and tools to write secure code
I've seen teams struggle with SA-8 implementation because they treat it like a documentation exercise. The secret is to focus on process integration. When your security architecture reviews become part of your regular development workflow (not a separate compliance activity), you start seeing real benefits. Your remediation costs drop, your products become more robust, and compliance becomes a natural byproduct of good engineering.
RA-3: Risk Assessment Done Right
.png)
Traditional risk assessment feels like filling out endless spreadsheets that nobody reads. RA-3 pushes for something better: systematic evaluation that actually drives decision-making.
What effective RA-3 implementation looks like in practice:
- Context-aware threat identification: Generic vulnerability lists won't cut it, you need threats specific to your architecture
- Quantified impact assessment: Understanding not just what could go wrong, but how bad it would be
- Decision integration: Risk assessment results that actually influence your development priorities
- Continuous updates: Risk isn't static, so your assessment process shouldn't be either
The challenge most product teams face with RA-3 is speed. Manual risk assessment processes can't keep up with modern development cycles. The solution is to automate intelligently. I've seen teams successfully implement continuous risk monitoring that integrates with their CI/CD pipelines, turning risk assessment from a bottleneck into an enabler.
CM-2: Configuration Management That Actually Works
Configuration management might sound boring, but CM-2 is where security theory meets operational reality. In a world of containers, microservices, and cloud-native architectures, traditional configuration management approaches fall flat.
.png)
The key components of effective CM-2 implementation include:
- Automated baseline documentation: Your security configurations should be captured as code
- Version control integration: Configuration changes need the same rigor as code changes
- Continuous monitoring: Drift detection that catches configuration changes before they become problems
- Pipeline integration: Configuration validation built into your deployment process
What I've found works best is treating security configurations as first-class citizens in your development process. When configuration management becomes part of your infrastructure-as-code approach, you get consistency, auditability, and agility all at once.
The Real Implementation Challenges (And How to Solve Them)
Implementing NIST 800-53 controls in a real development environment is hard. Not because the controls are bad, but because traditional compliance approaches clash with modern engineering practices.
The Documentation Trap
Every product security manager has been there, audit time rolls around, and you're scrambling to document security decisions that were made months ago. The documentation requirements in NIST 800-53 can feel overwhelming, especially when you're trying to move fast.
The solution isn't to generate less documentation, but to generate the right documentation at the right time. When your architecture reviews generate compliance evidence automatically, you solve two problems at once.
Resource Constraints at Scale
Implementing these controls manually doesn't scale. Period. If you're trying to manage NIST 800-53 compliance across multiple products with spreadsheets and manual reviews, you're setting yourself up for failure.
The answer is thoughtful automation. Not automation that removes human judgment, but automation that amplifies human expertise. When you can generate threat models automatically based on your actual architecture, your security experts can focus on the hard problems instead of the routine ones.
Continuous Compliance vs. Point-in-Time Audits
Here's a fundamental mismatch: traditional compliance focuses on proving your controls worked at a specific moment in time, but modern development practices require continuous integration and deployment.
The solution is to build continuous compliance into your development workflow. When every deployment automatically generates evidence of control implementation, you transform compliance from an event into a process.
Automation: The Game-Changer for NIST 800-53
I used to think automation was about reducing manual work. I was wrong. The real value of automation in NIST 800-53 implementation is consistency and scale.
Security Architecture Reviews at Development Speed
Traditional security architecture reviews can take weeks or months. Modern product development cycles are measured in days. This mismatch has killed more security programs than any technical challenge.
The breakthrough comes when you automate evidence collection while maintaining human oversight. Platforms that can connect to your existing development tools (Jira, Confluence, GitHub) and extract security context from real documentation change the game entirely. Instead of creating separate compliance artifacts, you're generating audit-ready evidence as a natural byproduct of your development process.
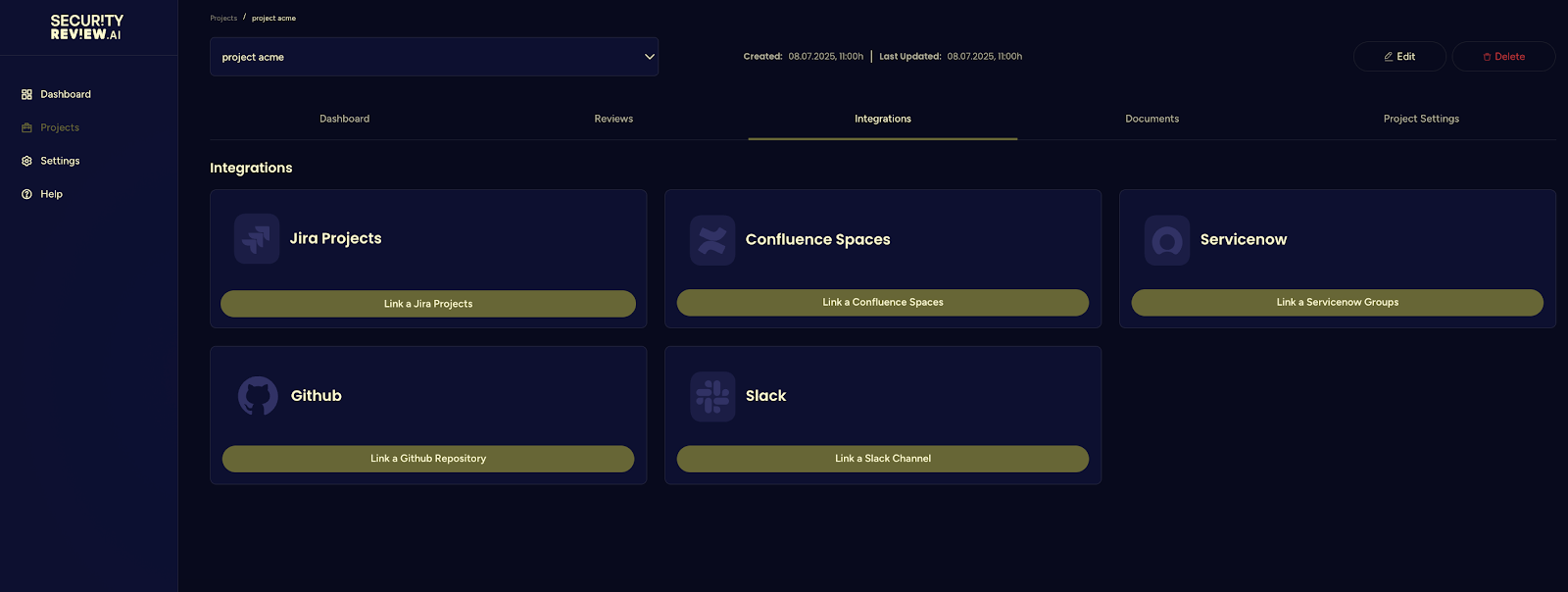
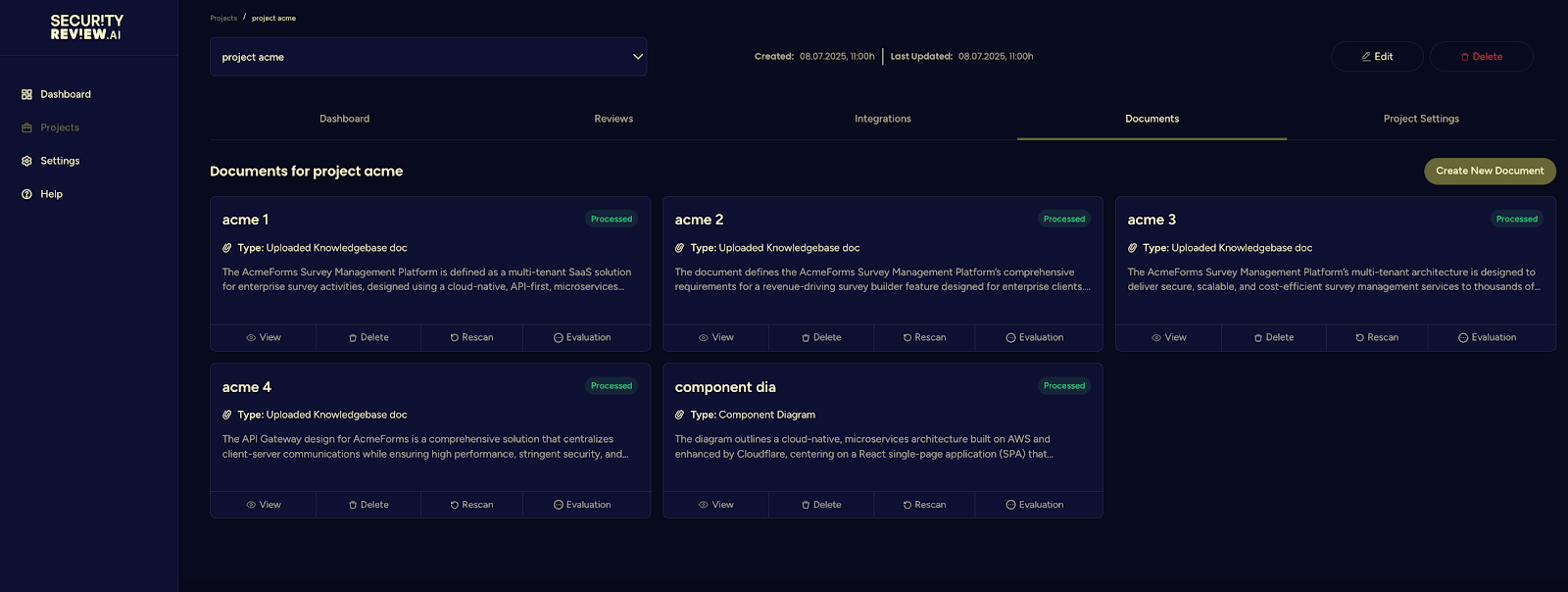
Risk Assessment as Continuous Process
The most effective risk assessment processes I've seen operate continuously, not periodically. When threat modeling becomes automated and integrated with your development workflow, you get ongoing risk visibility without disrupting development velocity.
The key is automation that's context-aware. Generic vulnerability scanners miss the nuances of your specific architecture. But automated threat modeling that understands your actual system design can identify risks that traditional approaches miss entirely.
Evidence Generation for Multiple Stakeholders
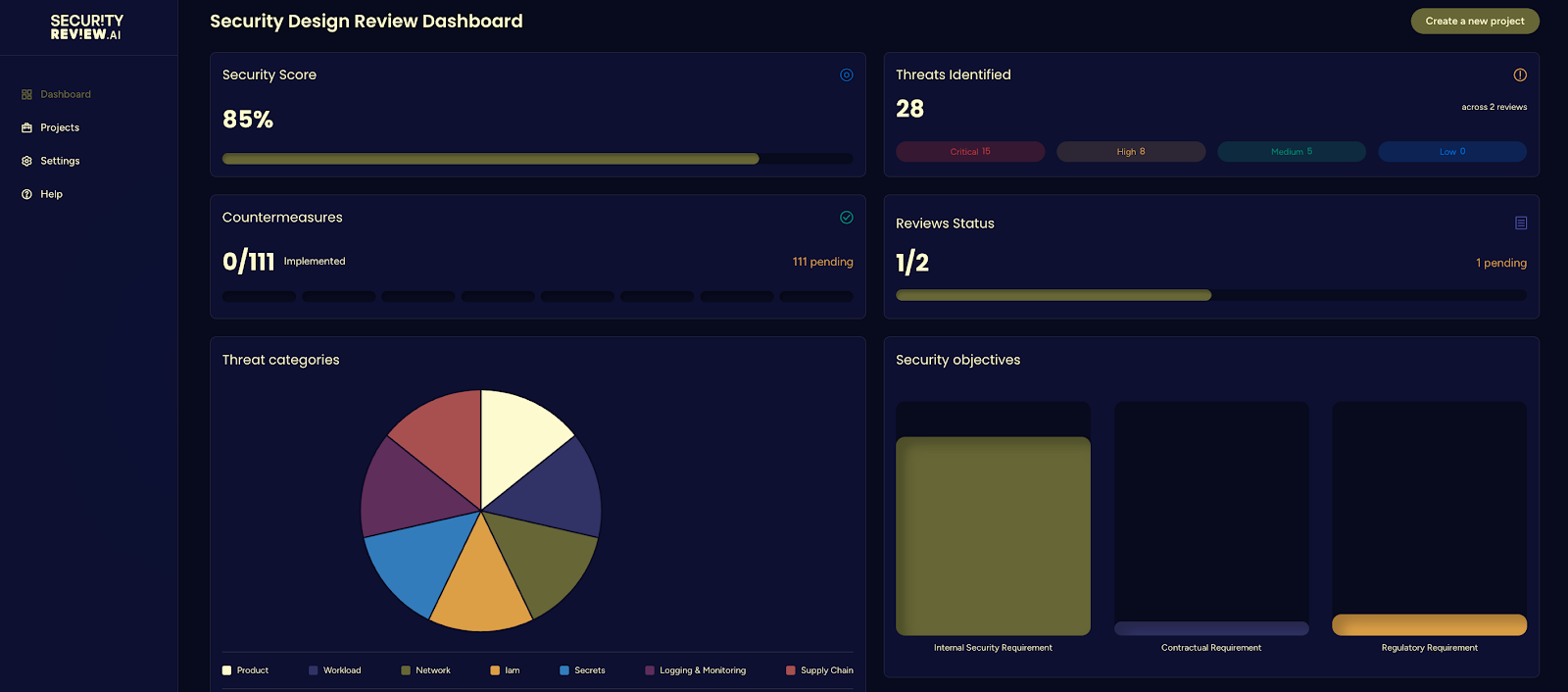

Different stakeholders need different views of the same security data:
- CISOs want executive summaries focusing on risk posture
- Developers need actionable security tickets in their workflow
- Auditors require comprehensive control mappings and evidence
- Compliance teams want detailed documentation aligned with regulatory requirements
The best implementations generate all of these views from the same underlying data, ensuring consistency while meeting each stakeholder's specific needs.
Making NIST 800-53 Work in Practice
.png)
Here's what I've learned from teams that successfully implement NIST 800-53 controls: it's all about building security thinking into your existing workflows.
Start with Integration
Don't begin by writing policies. Start by integrating security considerations into your existing development processes. When security architecture reviews become part of your regular design process, compliance documentation follows naturally.
Focus on Engineering-Driven Evidence
The most convincing audit evidence comes from rigorous engineering processes, not separate compliance activities. When your threat models are generated from actual system designs and your risk assessments reflect real architectural decisions, auditors trust your evidence because it's grounded in reality.
Build Continuous Monitoring
Static compliance doesn't work in dynamic environments. The teams that succeed with NIST 800-53 build continuous monitoring into their development pipelines. When every code change triggers an evaluation of security controls, you maintain compliance without slowing down development.
Embrace Tool Integration
Your security tools should work with your existing development infrastructure, not against it. The most successful implementations I've seen involve platforms that integrate seamlessly with tools teams are already using: GitHub for code, Jira for tracking, Confluence for documentation.
The Strategic Advantage of Getting This Right
When you implement NIST 800-53 controls thoughtfully, something interesting happens: compliance stops being a burden and starts being a competitive advantage.
Teams that master the integration of security controls into their development workflows don't just meet regulatory requirements—they build better products. They catch security issues earlier, reduce technical debt, and deploy with confidence.
The key insight is that NIST 800-53 controls, particularly SA-8, RA-3, and CM-2, aren't obstacles to good engineering—they're frameworks for systematic thinking about security. When implemented through engineering-driven processes rather than separate compliance activities, they enhance both security posture and development velocity.
The Role of Modern Security Review Platforms
Contemporary product security challenges demand sophisticated platforms that seamlessly integrate engineering excellence with regulatory compliance requirements. Organizations implementing NIST 800-53 controls increasingly benefit from automated solutions that streamline evidence collection, standardize documentation processes, and embed security reviews directly into development workflows without disrupting engineering velocity.
Platforms like SecurityReview.ai exemplify this evolution by transforming traditional security architecture reviews from manual and time-intensive processes into automated and continuous compliance activities. These platforms address the fundamental challenge product security teams face: maintaining rigorous NIST 800-53 compliance while supporting rapid development cycles and diverse technology stacks.
Remember, the goal is building products that are secure by design and can demonstrate that security to any stakeholder who needs to see it. When you get that balance right, compliance becomes what it should be: evidence of good engineering, not a separate burden on top of it.
FAQ
What is NIST 800-53 and why should product security teams care?
NIST Special Publication 800-53 provides a comprehensive set of security and privacy controls for information systems. Although originally designed for federal systems, it’s become an industry standard for building products that are secure by design. For modern engineering teams, it offers a blueprint for integrating security into the product development lifecycle, supporting both strong protection and regulatory compliance.
Do I need to implement all 1,000+ NIST 800-53 controls to be compliant?
No. While the framework is extensive, not all controls will apply to every product or organization. For most product development teams, the most relevant control families are: - System and Services Acquisition (SA) - Risk Assessment (RA) - Configuration Management (CM) Focusing on high-impact controls like SA-8, RA-3, and CM-2 can offer significant security benefits without unnecessary overhead.
What does “security by design” mean in the context of NIST 800-53?
“Security by design” means embedding security considerations into every stage of your product’s development, not retrofitting security measures at the end. NIST 800-53 supports this approach, encouraging teams to address security and privacy as a core aspect of their architecture and workflows, in alignment with shift-left practices.
What are the biggest implementation challenges, and how can they be overcome?
Common challenges include: - Excessive documentation requirements that slow down development - Resource constraints, especially in manual compliance processes - The need for continuous compliance rather than point-in-time audits Solutions focus on: - Automating documentation generation as part of daily workflows - Using automation and tool integration (with platforms like GitHub, Jira, or SecurityReview.ai) to reduce repetitive tasks - Embracing continuous risk assessment and monitoring integrated with CI/CD pipelines
How can we make documentation work for engineers, not against them?
Generate documentation as a natural outcome of your engineering process—for example, by integrating architecture reviews and change tracking into code and deployment workflows. Automation ensures the right evidence is always available without manual “paperwork sprint” before audits.
Are there tools or platforms that simplify NIST 800-53 compliance for engineers?
Yes. Modern security review platforms automate evidence collection, bridge engineering and compliance workflows, and provide tailored outputs for different stakeholders (e.g., CISOs, developers, auditors). These tools reduce manual effort and make compliance achievable at the speed of development.
What’s the difference between continuous compliance and a point-in-time audit?
- Point-in-time audits check if controls were in place at a specific past moment. - Continuous compliance ensures controls are validated with every code change or deployment, enabling faster releases and ongoing security visibility. How do SA-8, RA-3, and CM-2 controls map to daily engineering work? - SA-8 (Security and Privacy Engineering Principles): Integrates security into design decisions, promotes threat modeling, and ensures development teams are engaged and trained. - RA-3 (Risk Assessment): Focuses on automating risk identification and impact analysis that directly informs engineering priorities. - CM-2 (Configuration Management): Encourages use of infrastructure-as-code, automated drift detection, and embedding configuration checks into deployment pipelines.
How do you generate audit-ready evidence without slowing down releases?
By connecting your security and compliance tools to systems already used in development (like GitHub for code, Jira for tasks, and Confluence for documentation), you create compliance artifacts as a byproduct of normal work, not as an additional requirement.
Can thoughtful NIST 800-53 implementation actually speed up product delivery?
Yes. When controls are integrated into engineering workflows and supported by the right automation, compliance transitions from a manual bottleneck to an enabler. Teams spot security issues earlier, fix them faster, and deploy with greater confidence.















