DORA: A Comprehensive CIO/CISO's Guide to Operational Resilience Through Threat Modeling and Security Architecture Reviews

The Digital Operational Resilience Act (DORA) represents the most transformative regulatory shift in financial services cybersecurity since the inception of modern banking technology. As someone who has spent the better part of the last decade implementing security controls across multiple regulatory frameworks, I can confidently say that DORA is different it's not just another compliance checkbox, but a fundamental reimagining of how we approach digital operational resilience.
For CISOs and CIOs leading product security teams, the question isn't whether DORA will transform your security program—it's how quickly you can adapt your threat modeling and security architecture review practices to not just meet compliance, but to genuinely strengthen your organization's defensive posture. With enforcement now in full effect since January 17, 2025, and penalties reaching up to 2% of global turnover for financial institutions, the stakes have never been higher.
Understanding DORA's Revolutionary Approach to Digital Resilience
DORA, officially Regulation (EU) 2022/2554, became enforceable on January 17, 2025, and applies to approximately 22,000 financial entities across the EU. Unlike previous regulations that primarily focused on capital allocation for operational risks, DORA establishes a comprehensive framework specifically targeting Information and Communication Technology (ICT) risks with unprecedented scope and depth.
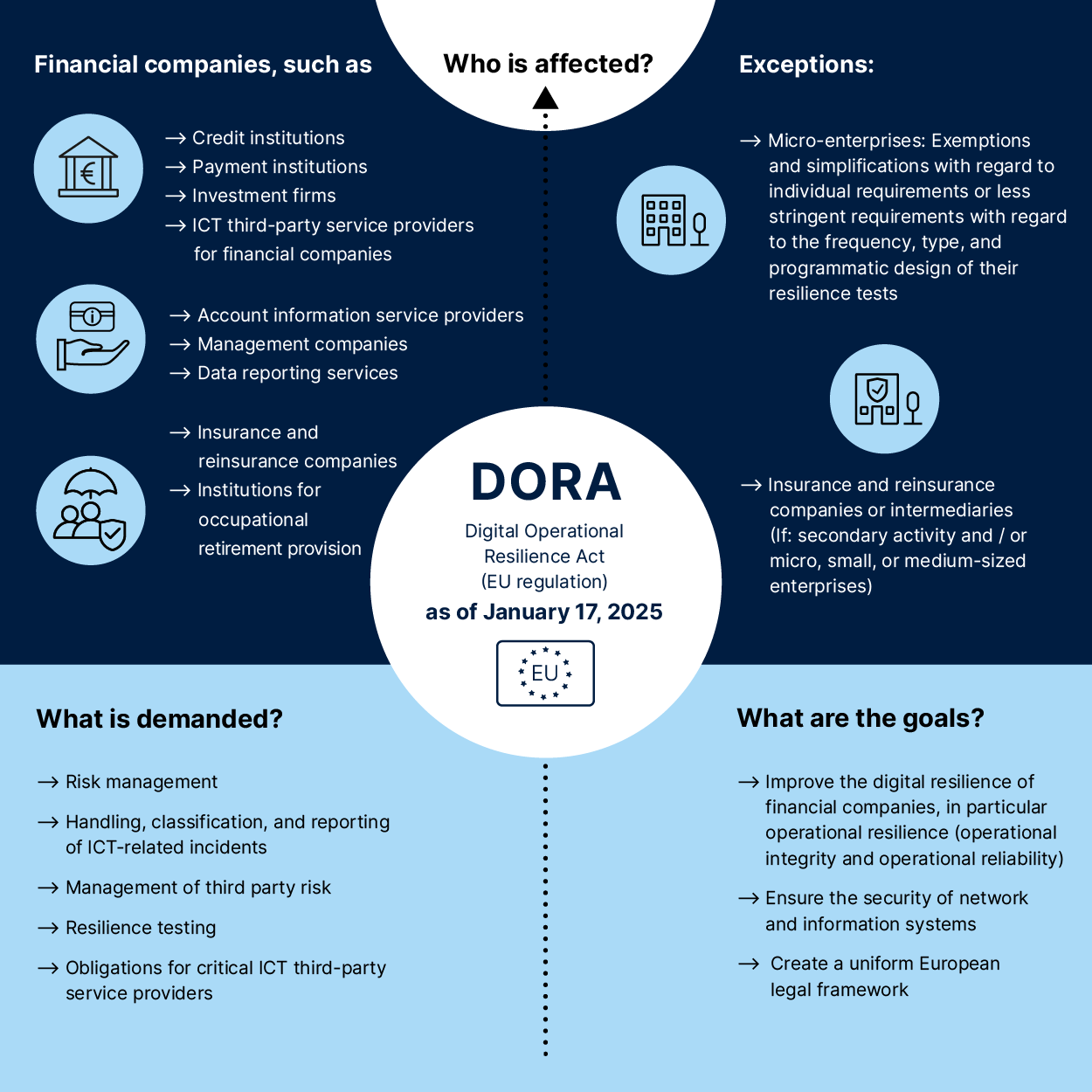
The regulation recognizes a fundamental truth that many of us in security leadership have been advocating for years: ICT incidents and operational failures can threaten financial system stability regardless of adequate capital reserves. This shift from reactive capital allocation to proactive operational resilience represents a maturation of regulatory thinking that aligns perfectly with modern threat modeling methodologies.
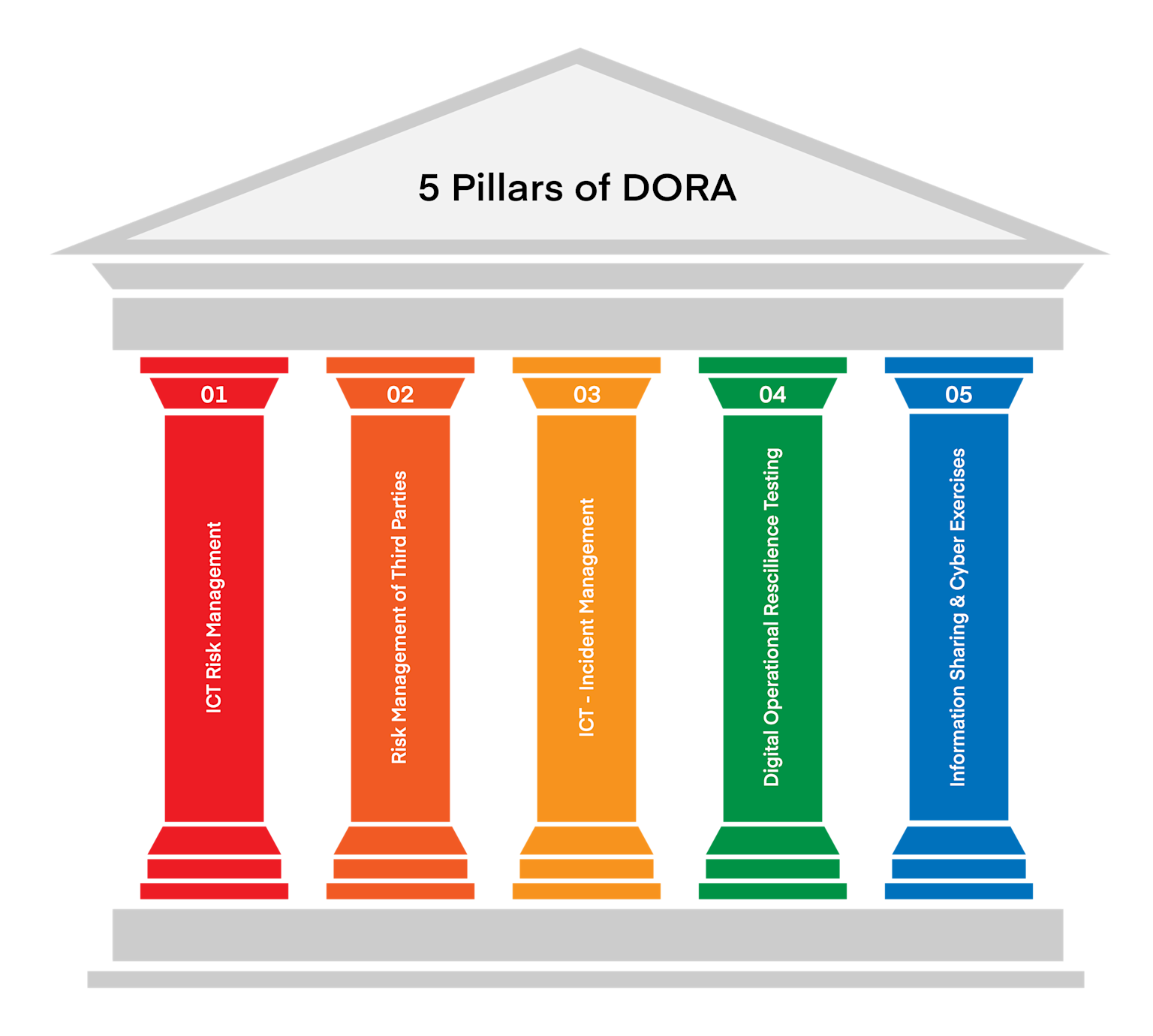
What sets DORA apart is its explicit focus on five interconnected pillars:
- ICT Risk Management - Comprehensive frameworks for identifying and managing technology risks through systematic approaches
- ICT-Related Incident Management and Reporting - Structured processes for detecting, classifying, and reporting ICT incidents within strict timelines
- Digital Operational Resilience Testing - Mandatory assessment of systems through various testing methodologies including Threat-Led Penetration Testing (TLPT)
- ICT Third-Party Risk Management - Comprehensive oversight of critical technology service providers with mandatory exit strategies
- Information Sharing - Collaborative threat intelligence and best practice sharing within trusted financial communities
DORA Compliance Assessment Process for Product Security Teams - Generated using ChatGPT, please check for copyright issues before publishing
The Strategic Context: Why Traditional Approaches Are Insufficient
Having implemented countless security frameworks over the years, I've observed a consistent pattern: organizations typically approach compliance through policy development and control implementation, but they often miss the foundational work that makes these controls effective. This is where most DORA implementation efforts are already falling short, particularly given the regulation's comprehensive scope and strict enforcement timeline.
The Asset Discovery and Documentation Challenge
Article 8 of DORA requires financial entities to "identify, classify and adequately document all ICT supported business functions, roles and responsibilities, and the information assets supporting such functions". This seemingly straightforward requirement exposes the most significant gap in most organizations' security programs and represents a foundational element that underpins all other DORA requirements.
Traditional asset management approaches rely heavily on configuration management databases (CMDBs) and network scanning tools. However, these methods often miss the nuanced relationships between business functions, data flows, and supporting technologies that DORA explicitly requires. Without this foundational understanding, threat modeling becomes an academic exercise rather than practical risk management that can support regulatory compliance.
The Incident Classification and Reporting Sophistication Gap
DORA's incident management requirements under Articles 17-20 introduce a sophisticated classification system that goes far beyond traditional incident response. Financial entities must now classify incidents as "major" based on specific criteria including:
- Successful malicious and unauthorized access that may result in data losses
- Material impact on two or more criteria including affected customers, reputational impact, incident duration, geographical spread, and economic impact
- Cumulative impact assessment where recurring incidents may be classified as major when viewed collectively
The regulation mandates reporting timelines as short as 4 hours for initial notifications of major incidents, with intermediate and final reports required within specific timeframes. This represents a significant departure from traditional incident response timelines and requires sophisticated detection and classification capabilities.
The Third-Party Risk Management Complexity
DORA's approach to third-party risk management, outlined in Articles 28-44, introduces unprecedented requirements for managing ICT service provider relationships. The regulation establishes a direct oversight framework for "Critical ICT Third-Party Service Providers" (CTPPs), with the European Supervisory Authorities (EBA, ESMA, EIOPA) serving as Lead Overseers.
Financial entities must now maintain comprehensive registers of all ICT third-party arrangements and implement mandatory exit strategies for critical services. These exit strategies must address both planned and unplanned scenarios, including provider failure, contract termination, and service degradation.
How Advanced Threat Modeling Addresses DORA's Complex Requirements
Systematic Risk Identification Under Article 6's ICT Risk Management Framework
The ICT Risk Management Framework required by Article 6 mandates "strategies, policies, procedures, and ICT tools that aim at ensuring the resilience, continuity and availability of ICT systems". Advanced threat modeling directly supports this requirement by providing a systematic methodology for identifying potential attack vectors before they can be exploited, but more importantly, it creates the foundational documentation that DORA requires.
Modern threat modeling approaches, particularly when supported by platforms that can integrate with existing documentation and development workflows, transform the compliance burden from a separate activity into a natural byproduct of good security engineering practices. When SecurityReview.ai processes existing documentation alongside threat modeling exercises, it automatically generates the traceability and documentation that DORA Article 8 requires.
Enhanced Asset Mapping and Business Function Documentation
Article 8's identification requirements become significantly more manageable when supported by comprehensive threat modeling practices. The process of developing threat models naturally produces detailed documentation of:
- Business function dependencies - Understanding which ICT systems support critical business operations and how failures cascade
- Data flow mappings - Documenting how sensitive information moves through systems, including cross-border data transfers
- Trust boundaries and attack surfaces - Identifying points where security controls must be enforced and potential entry points for malicious actors
- Integration points and dependencies - Mapping third-party service integrations and their criticality to business operations
Organizations implementing mature threat modeling practices often find that they've already addressed 60-70% of Article 8's documentation requirements through their modeling exercises, significantly reducing the compliance burden.
Informed Testing Strategy Development for TLPT Compliance
DORA's testing requirements, particularly TLPT mandated under Article 26, benefit enormously from well-developed threat models. Rather than conducting generic penetration tests, threat models provide the foundation for creating realistic attack scenarios that reflect actual risks to your organization and align with the regulation's requirements for threat intelligence-driven testing.
TLPT must be conducted at least every three years for critical financial entities and must simulate the tactics, techniques, and procedures of real threat actors using current threat intelligence. This approach transforms TLPT from a compliance exercise into a genuine capability assessment that validates both technical controls and operational response procedures.
Security Architecture Reviews: The Compliance Foundation
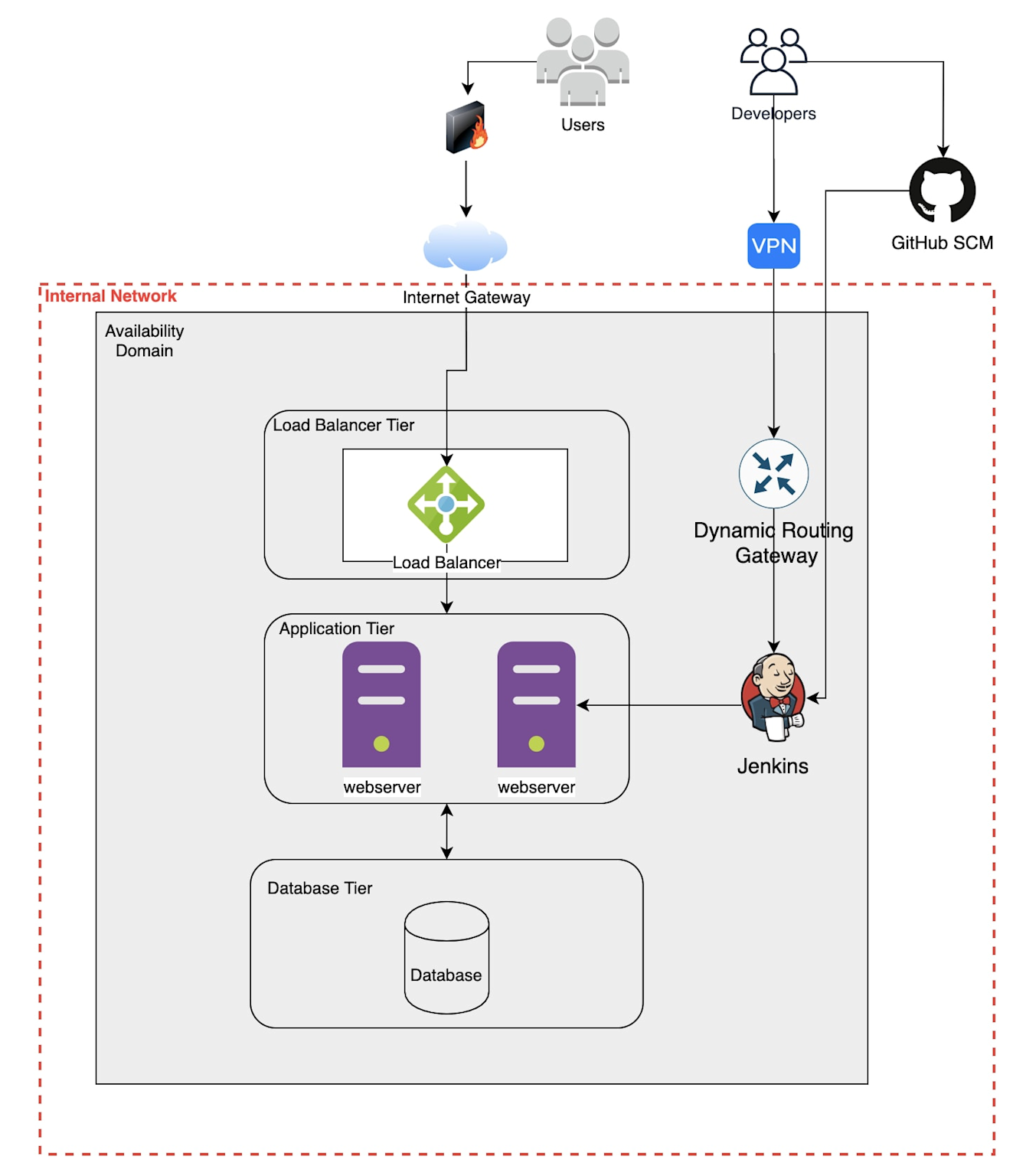
Diagram showing security architecture review layers in a cloud-native environment including load balancers, web servers, database, VPN, dynamic routing, Jenkins integration, and GitHub SCM. - Generated using ChatGPT, please check for copyright issues before publishing
Validating Control Effectiveness and Regulatory Alignment
While threat modeling identifies what could go wrong, security architecture reviews validate that your defensive measures will actually work when tested and align with DORA's specific requirements. Article 8 requires continuous monitoring and control of ICT systems, which demands architecture that can support real-time visibility and response capabilities mandated by the regulation.
Security architecture reviews examine whether your current design patterns can support DORA's monitoring and response requirements, including:
- Logging and monitoring architectures - Can you detect and classify incidents as required by DORA's incident reporting pillar within the mandated 4-hour window?
- Network segmentation designs - Do you have the ability to "instantaneously sever" connections as Article 8 requires?
- Backup and recovery architectures - Are your business continuity measures architecturally sound and do they meet Article 11's specific requirements?
- Third-party integration security - Can you monitor and control third-party access as required for critical service providers?
Article 11 Backup and Recovery Architectural Requirements
DORA's Article 11 establishes detailed backup and recovery requirements that directly impact architectural decisions. Financial entities must develop backup policies specifying scope and frequency based on data criticality, and implement recovery methods that ensure minimal downtime.
Critically, the regulation requires that backup systems use "ICT systems that have an operating environment different from the main one, that is not directly connected with the latter and that is securely protected from any unauthorized access or ICT corruption". This mandates architectural separation that goes beyond traditional backup approaches and requires careful design consideration.
For systemically important entities, Article 11 also requires maintaining "at least one secondary processing site endowed with resources, capabilities, functionalities and staffing arrangements sufficient and appropriate to ensure business needs". This secondary site must be geographically separated to ensure distinct risk profiles and immediately accessible to ensure continuity.
Third-Party Integration Security and Exit Strategy Architecture
DORA's third-party risk management requirements are particularly challenging because they extend responsibility beyond your direct control and require architectural considerations for service provider integration and disengagement. Security architecture reviews provide a systematic way to evaluate how third-party services integrate with your core systems and what additional controls may be necessary.
Exit strategies, mandated under DORA for critical ICT services, must be architecturally feasible. This means:
- Data portability mechanisms - Can you extract and migrate data without service provider cooperation?
- Service abstraction layers - Are critical services architected to enable provider substitution?
- Monitoring and control retention - Can you maintain oversight during transition periods?
Advanced Implementation Scenarios: Real-World DORA Compliance
Scenario 1: Payment Processing System Under DORA's Comprehensive Framework
Consider a financial institution developing a new real-time payment processing system that must comply with DORA's full requirements. A comprehensive threat model would identify potential attack vectors including:
- API abuse scenarios - Attackers attempting to manipulate transaction amounts, destinations, or processing logic
- Timing attack vectors - Exploiting processing delays to conduct arbitrage attacks or market manipulation
- Data exfiltration risks - Unauthorized access to transaction logs, customer data, or financial intelligence
- Third-party integration vulnerabilities - Risks from payment networks, clearing systems, and regulatory reporting integrations
The corresponding security architecture review would validate that:
- Rate limiting and input validation controls can prevent API abuse and meet DORA's incident prevention requirements
- Transaction processing includes appropriate integrity checks and audit trails for incident investigation
- Logging architecture captures sufficient detail for DORA's incident reporting requirements within mandated timelines
- Network segmentation isolates payment processing from other systems and enables rapid isolation if required
- Backup and recovery systems meet Article 11's geographic separation and operational independence requirements
- Third-party integrations include monitoring capabilities and exit strategy mechanisms
When these activities are supported by automated platforms, organizations can generate DORA-compliant documentation that maps identified threats to specific controls, demonstrates how architecture decisions address regulatory requirements, and maintains the traceability that supervisory authorities expect.
Scenario 2: Cloud Service Integration with DORA Third-Party Oversight
Financial institutions increasingly rely on cloud services for everything from data analytics to customer relationship management. DORA requires specific attention to these third-party relationships, particularly for services supporting critical functions, and introduces direct oversight of critical providers by European Supervisory Authorities.
Threat modeling for cloud integration under DORA might identify:
- Shared responsibility gaps - Areas where it's unclear whether the cloud provider or customer is responsible for specific security controls, creating compliance risks
- Data residency and sovereignty risks - Potential for sensitive data to be processed or stored in unauthorized jurisdictions, violating DORA's data protection requirements
- Service availability dependencies - Single points of failure that could disrupt critical business functions and trigger major incident reporting requirements
- Regulatory access and audit risks - Challenges in meeting DORA's audit and oversight requirements when services are provided by third parties
Architecture reviews would then validate:
- Contract terms alignment - Whether service level agreements support DORA's incident reporting timelines and third-party oversight requirements
- Technical control implementation - Proper configuration of identity and access management, encryption, and monitoring that meets DORA standards
- Exit strategy viability - Whether you can actually implement the exit strategies that DORA mandates, including data portability and service continuity
- Regulatory compliance support - Whether the provider can support DORA's audit and oversight requirements, including potential ESA examinations
Scenario 3: Information Sharing Architecture for Article 45 Compliance
DORA's Article 45 mandates information sharing arrangements for cyber threat intelligence within trusted communities of financial entities. This requires architectural considerations for secure information exchange while maintaining confidentiality and compliance with competition law.
Implementation considerations include:
- Secure communication channels - Platforms that ensure confidentiality, integrity, and availability of shared threat intelligence
- Data classification and handling - Systems that protect sensitive information while enabling effective collaboration
- Automated threat intelligence integration - Capabilities to consume and act on shared indicators of compromise and attack patterns
- Audit and compliance tracking - Mechanisms to demonstrate appropriate use of shared information and compliance with participation rules
Architecture reviews must validate that information sharing systems meet DORA's requirements for protecting "potentially sensitive nature of the information shared" while enabling the collaborative threat response that the regulation envisions.
Comprehensive Compliance Challenges and Advanced Solutions
Over-Reliance on Generic Frameworks in a Specific Regulatory Context
Many organizations attempt to address DORA requirements by implementing standard frameworks like ISO 27001 or NIST Cybersecurity Framework. While these frameworks provide valuable structure, they don't address the specific business context, regulatory timelines, and enforcement mechanisms that DORA demands.
Effective DORA implementation requires threat models and architecture reviews that are tailored to:
- Specific regulatory requirements - Controls must demonstrably address DORA's articles and requirements
- Enforcement timelines - Systems must support the rapid incident detection and reporting that DORA mandates
- Supervisory expectations - Documentation and processes must meet the standards that ESAs will enforce
- Business context - Risk assessments must reflect your specific business functions, technology stack, and threat landscape
Generic frameworks should inform your approach, but they cannot substitute for DORA-specific analysis and implementation.
Treating Compliance as a Point-in-Time Exercise vs. Continuous Resilience
DORA explicitly requires continuous monitoring and regular updates to risk assessments. The regulation's emphasis on ongoing testing, incident learning, and adaptation means that compliance is not a destination but a continuous journey of improvement.
Organizations that treat threat modeling and architecture reviews as annual exercises will struggle to maintain compliance as their technology environments evolve and new threats emerge. Successful DORA implementations integrate these activities into ongoing development and operational processes through:
- Continuous threat model updates - Models that evolve with system changes and new threat intelligence
- Integrated architecture reviews - Reviews that are part of change management and deployment processes
- Automated compliance monitoring - Systems that continuously validate control effectiveness and regulatory alignment
- Regular testing and validation - Ongoing verification that controls work as designed and meet evolving requirements
Inadequate Documentation and Regulatory Traceability
DORA requires extensive documentation not just of what controls you have implemented, but of how those controls address specific risks and regulatory requirements. The regulation's enforcement approach will focus heavily on the ability to demonstrate compliance through clear documentation and traceability.
Effective DORA documentation should clearly link:
- Identified threats to specific business risks - Demonstrating understanding of potential impact
- Architecture decisions to threat mitigation strategies - Showing how design choices address identified risks
- Control implementations to regulatory requirements - Mapping controls to specific DORA articles and requirements
- Testing results to threat model assumptions - Validating that models accurately reflect real-world risks
- Incident outcomes to control improvements - Demonstrating continuous improvement based on operational experience
Enforcement Reality: Understanding DORA's Penalty Framework
DORA's enforcement mechanisms represent some of the most stringent penalties in EU financial regulation. The European Supervisory Authorities have made clear that they expect comprehensive compliance from the January 17, 2025 effective date, with no grace period for implementation.
Financial Penalties and Enforcement Scope
The regulation establishes a comprehensive penalty framework that affects both institutions and individuals:
- Financial institutions face fines up to 2% of total annual worldwide turnover or 1% of average daily turnover
- Individual executives can be fined up to €1,000,000 for compliance failures
- Critical ICT third-party providers face penalties up to €5,000,000, with individual executives facing up to €500,000
- Continuous non-compliance can result in daily fines for up to six months until compliance is achieved
Importantly, these penalties can be combined with operational restrictions, business limitations, and public disclosure of violations, creating significant reputational and operational risks beyond financial impact
Supervisory Authority Powers and Approach
The European Supervisory Authorities (EBA, ESMA, EIOPA) have been granted extensive powers under DORA, including:
- Investigatory powers - Authority to conduct audits, request documentation, and inspect cybersecurity measures
- Direct oversight of critical providers - Ability to oversee ICT service providers directly through Lead Overseer arrangements
- Penalty imposition - Authority to impose administrative penalties and publish violations
- Operational restrictions - Power to limit business activities or suspend operations for severe non-compliance
The ESAs have established Joint Examination Teams (JETs) to conduct oversight activities and have made clear their intention to take a robust approach to enforcement from day one.
Building Sustainable DORA Compliance Capabilities
Integration with Development and Operational Workflows
The most successful DORA implementations integrate threat modeling and architecture reviews directly into development and operational workflows, making compliance a natural outcome of good security practices rather than a separate burden:
- Design reviews include DORA-aligned threat modeling - New systems and services undergo threat analysis that directly supports regulatory requirements
- Architecture reviews gate deployment decisions - Systems cannot be deployed to production without architectural security validation that addresses DORA requirements
- Continuous testing validates regulatory assumptions - Regular security testing confirms that identified threats remain relevant and controls meet DORA standards
- Incident response feeds back into models - Operational experience continuously improves threat models and architectural decisions
Executive Visibility and Regulatory Governance
DORA places explicit responsibility on management boards and senior executives for ICT risk management, making executive engagement essential for compliance. Under Ireland's Senior Executive Accountability Regime (SEAR), DORA has been classified as a 'prescribed contravention,' mandating that senior executives take reasonable steps to ensure compliance.
Executives need dashboards and reporting that provide:
- Business function risk exposure - Clear visibility into which critical services face the highest threat levels and regulatory risks
- Control effectiveness metrics - Evidence that implemented security measures are working as intended and meeting DORA standards
- Compliance status indicators - Real-time visibility into DORA requirement fulfillment across all five pillars
- Resource allocation recommendations - Data-driven guidance on where additional investment would most effectively reduce risk and ensure compliance
Continuous Capability Improvement and Regulatory Adaptation
DORA's emphasis on testing and validation creates natural feedback loops that should drive continuous improvement in threat modeling and architecture review practices. Each TLPT exercise should validate existing threat models and identify new attack vectors. Architecture reviews should be updated based on operational experience, incident learnings, and evolving regulatory expectations.
Organizations that treat these activities as learning exercises rather than compliance checkboxes develop more mature security capabilities and achieve better business outcomes while maintaining regulatory compliance.
Advanced Third-Party Risk Management Under DORA
Critical Provider Designation and Oversight
DORA introduces a revolutionary approach to third-party risk management through direct oversight of Critical ICT Third-Party Service Providers (CTPPs). The European Supervisory Authorities assess providers based on:
- Systemic impact - The potential disruption if the provider experiences failure
- Systemic importance of clients - The number of globally or systemically important institutions relying on the provider
- Criticality of supported functions - The importance of business functions supported by the provider
- Degree of substitutability - The availability of alternative providers and migration costs
Once designated as critical, providers become subject to direct ESA oversight through Lead Overseers, including information requests, investigations, inspections, and recommendations. This creates a two-tier compliance approach where financial entities must manage their own DORA compliance while also ensuring their critical providers meet ESA oversight requirements.
Mandatory Exit Strategy Implementation
DORA requires comprehensive exit strategies for all critical ICT outsourcing arrangements, representing one of the most practical and challenging aspects of the regulation. These strategies must address:
- Contractual safeguards - Clear termination rights, notice periods, and service continuity obligations
- Data ownership and portability - Protocols for data return, migration, and secure destruction
- Service continuity during transition - Mechanisms to maintain operations during provider changes
- Knowledge transfer requirements - Documentation and personnel support during exits
- Alternative provider identification - Pre-qualified alternatives and rapid onboarding procedures
Exit strategies must be tested regularly through simulations and scenario planning to ensure viability in both planned and emergency scenarios. This testing requirement means that exit strategies cannot be theoretical documents but must be operationally validated plans.
Information Sharing and Threat Intelligence Integration
Article 45 Implementation for Collaborative Defense
DORA's information sharing requirements under Article 45 mandate that financial entities participate in collaborative threat intelligence sharing within trusted communities. This sharing must include:
- Indicators of compromise (IoCs) - Technical indicators of malicious activity
- Tactics, techniques, and procedures (TTPs) - Behavioral patterns of threat actors
- Cybersecurity alerts - Real-time warnings about emerging threats
- Configuration tools - Security tools and configurations that improve collective defense
The regulation requires that information sharing occurs within "trusted communities of financial entities" and includes protections for sensitive information while respecting competition law and data protection requirements. Financial entities must notify competent authorities of their participation in such arrangements.
Practical Implementation of Threat Intelligence Sharing
Effective DORA-compliant information sharing requires:
- Secure communication platforms - Technical infrastructure that protects shared intelligence while enabling rapid dissemination
- Automated threat intelligence integration - Systems that can consume shared indicators and automatically update defensive measures
- Legal and compliance frameworks - Agreements that protect participants while enabling effective collaboration
- Operational procedures - Processes for contributing to and acting on shared intelligence while maintaining business confidentiality
Organizations like FS-ISAC provide platforms that specifically address DORA's Article 45 requirements, enabling financial institutions to meet regulatory obligations while benefiting from collective threat intelligence.
The SecurityReview.ai Advantage in DORA Implementation
Automated Documentation and Regulatory Traceability
When implementing DORA compliance through traditional manual approaches, organizations often struggle with the documentation and traceability requirements that regulators expect. SecurityReview.ai addresses this challenge by automatically generating DORA-aligned documentation as a natural byproduct of threat modeling and architecture review processes.
The platform integrates with existing development and operational tools—Jira, Confluence, Google Docs, ServiceNow, GitHub—to create comprehensive security reviews that directly address DORA's requirements without requiring teams to learn new tools or create separate compliance artifacts.
Intelligent Gap Analysis and Continuous Improvement
SecurityReview.ai's recursive questioning engine addresses one of the most significant challenges in DORA implementation: ensuring completeness and accuracy of risk assessments. The platform identifies missing context, asks clarifying questions, and finds answers within existing documentation, significantly reducing the hallucination risk that often affects manual compliance efforts.
This approach transforms DORA compliance from a point-in-time exercise into a continuous improvement process, where threat models and architecture reviews evolve with changing systems and threat landscapes while maintaining regulatory alignment.
Integration with DORA-Specific Requirements
The platform's ability to process and integrate diverse information sources—from architectural documentation to threat intelligence to operational procedures—makes it particularly well-suited for DORA's comprehensive requirements. Rather than treating compliance as a separate activity, SecurityReview.ai embeds DORA considerations into standard security engineering practices, making compliance a natural outcome of good security design.
The Path Forward: From Compliance to Operational Excellence
DORA represents more than regulatory compliance—it's an opportunity to fundamentally improve how financial institutions approach digital operational resilience. Organizations that embrace this opportunity through mature threat modeling and security architecture review practices will not only meet regulatory requirements but will build genuinely more resilient operations that provide competitive advantage.
The regulation's comprehensive scope, strict enforcement mechanisms, and continuous improvement requirements mean that success requires a fundamental shift from compliance-focused to resilience-focused thinking. Threat landscapes evolve, business requirements change, and technology architectures adapt. The organizations that will thrive under DORA are those that build adaptive capabilities rather than static compliance programs.
Strategic Recommendations for CISOs and CIOs
- Start with solid foundations - Invest in comprehensive threat modeling and security architecture review capabilities that directly address DORA's requirements
- Leverage automation and integration - Use platforms that make DORA compliance a natural byproduct of security engineering rather than a separate burden
- Focus on business value beyond compliance - Build capabilities that deliver operational resilience and business advantage, not just regulatory checkbox completion
- Prepare for continuous evolution - Develop capabilities that can adapt to changing regulations, threats, and business requirements
- Invest in executive engagement - Ensure senior leadership understands both the regulatory risks and the business opportunities that DORA represents
The Enforcement Reality and Future Outlook
With DORA enforcement now active and the European Supervisory Authorities taking a strict approach to compliance, organizations can no longer treat this as a future concern. The regulation's comprehensive penalty framework, including personal liability for executives and potential business restrictions, means that non-compliance carries existential risks for financial institutions.
However, organizations that have implemented comprehensive threat modeling and security architecture review practices aligned with DORA's requirements are finding that compliance becomes a manageable outcome of good security engineering. The key is recognizing that DORA compliance is not a destination but an ongoing journey of continuous improvement in digital operational resilience.
The deadline for DORA compliance has passed, but the work of building truly resilient digital operations continues to evolve. The question is not whether your organization will adapt to DORA's requirements, but whether you will use this regulatory moment to build the security capabilities your business needs to thrive in an increasingly digital and threatening environment. Organizations that get this right will find that DORA compliance becomes a competitive advantage rather than a compliance burden.















