Over 50% of organizations have experienced external attacks attributed to software security flaws. Traditional manual threat modeling approaches are struggling to keep pace with the speed of modern development cycles. SecurityReview.AI represents a paradigm shift toward AI-native threat modeling, offering enterprises a comprehensive solution that accelerates security architecture review without sacrificing depth or relevance. This whitepaper explores how SecurityReview.AI addresses fundamental challenges in threat modeling through its innovative PWNISMS framework, advanced AI processing capabilities, and seamless integration with existing product development (SDLC) workflows.
The Crisis in Traditional Threat Modeling
Traditional threat modeling faces a perfect storm of challenges that render it increasingly inadequate for modern enterprise security needs. Manual process complexity dominates the landscape, with security architects spending weeks or months gathering information from disparate sources, conducting stakeholder interviews, and cross-referencing threat databases.
This process saturation creates significant bottlenecks, particularly for organizations lacking experienced security architects who can navigate the numerous available threat modeling frameworks and validation methodologies.
Scalability emerges as perhaps the most critical limitation. The 2021 BSIMM survey revealed an average ratio of one Software Security Group member per 140 software developers, with each security team member supporting over 50 applications. This resource constraint forces organizations to prioritize only their most critical applications for comprehensive threat modeling, leaving substantial portions of their application portfolio potentially vulnerable to attacks.
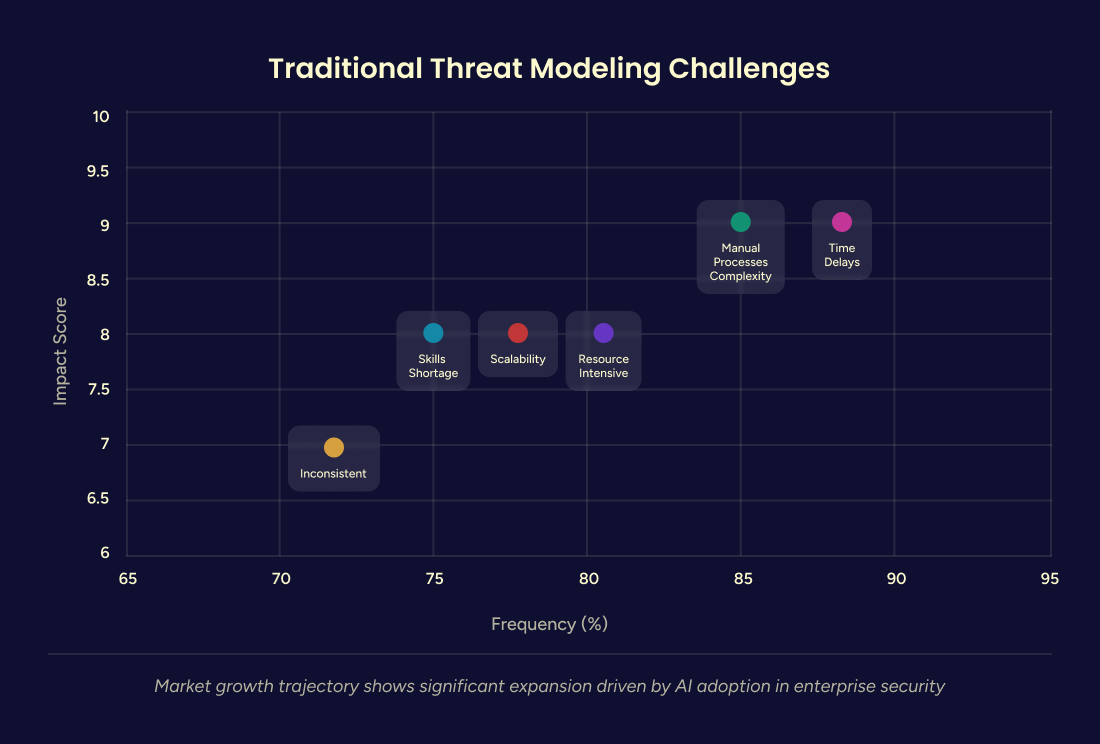
The consistency problem compounds these challenges, as the thoroughness and effectiveness of manual threat modeling exercises depend heavily on the experience and judgment of those conducting them. Different practitioners have varying expectations of what constitutes a threat, how threat models should be structured, and how threats should be ranked. This inconsistency creates downstream complications in aligning on priority threats and determining which countermeasures development teams should implement first.
Modern applications exacerbate these challenges as they are increasingly being built on contemporary distributed microservices architectures and not as monoliths. As applications scale and migrate to cloud environments, development teams often assume full-stack management responsibilities that were previously handled by dedicated IT infrastructure teams. The threat model must now account for expanded infrastructure responsibilities, scope changes, complex topologies, and associated risks—a task that proves overwhelming for development teams without specialized security expertise.
Unrecognized entry points and trust boundaries present another critical challenge, particularly in cloud environments. With major cloud service providers like Amazon Web Services, Azure and GCP, many entry points remain unrecognized, including publicly-exposed management APIs and services. This complexity makes Data Flow Diagrams (DFDs) and Process Flow Diagrams (PFDs) significantly more intricate than traditional known entry points would suggest.
SecurityReview.AI: Revolutionizing Threat Modeling Through AI
SecurityReview.AI fundamentally reimagines threat modeling by leveraging artificial intelligence to address the core limitations of traditional approaches. As an AI-native product, it processes and generates threat scenarios and countermeasures based on inputs provided by product teams, regardless of how unstructured these inputs may be.
Comprehensive Integration Capabilities
The platform's strength lies in its extensive integration ecosystem, designed to gather information from wherever product teams naturally collaborate and document their work. SecurityReview.AI seamlessly connects with Jira, Confluence, GitHub, Google Docs, SharePoint, Slack, Microsoft Teams, and ServiceNow. It can even consume & process product team standup meeting recordings (both audio & video) where product teams discuss features, capabilities, and system architectures.
This integration capability addresses one of the most time-consuming aspects of traditional threat modeling—the information gathering phase. Rather than requiring security engineers to conduct multiple interviews and hunt through scattered documentation, SecurityReview.AI automatically aggregates relevant information from these diverse sources, significantly reducing the initial overhead of threat modeling exercises.
Advanced AI Processing Architecture
At its core, SecurityReview.AI employs a sophisticated multi-modal AI processing architecture that transforms unstructured data into actionable security insights. The system begins by converting all input data into text format, using reasoning models to analyze images, diagrams, flowcharts, and other visual elements within documents. This ensures that no critical architectural information is lost during the analysis process.
Recursive summarization forms a critical component of the processing pipeline. When documents exceed the context limits of underlying AI models, the system intelligently chunks content and generates individual summaries before creating comprehensive overviews. This approach ensures that large, complex architectural documents receive thorough analysis without losing important details.
Vector Database and Knowledge Management
SecurityReview.AI employs advanced vector database technology to enable sophisticated contextual analysis and retrieval. The system stores processed documents as vectors, which retain semantic meaning while enabling rapid similarity searches and contextual retrieval. This vector-based approach allows the system to identify relationships between seemingly unrelated pieces of information and surface relevant context that might otherwise be missed.
The platform maintains multiple vector databases to ensure comprehensive threat analysis:
Document Vector Database: Stores all processed project/application documentation, enabling contextual retrieval during analysis
Threat, Test cases, & Countermeasure Database: Contains expertly curated threat scenarios, attack patterns, countermeasures, and best practices accumulated over fifteen years of threat modeling, security architecture and product security experience
Security Knowledge Base (SKB): Maintains current threat intelligence and vulnerability information for a large selection of commonly used underlying application components such as Storage & Compute systems, Web Servers, Search & query systems, Message Queues, SCMs and CI/CD systems. The SKB utilises automated deep research agents to gather the latest threat scenarios, countermeasures and security best practices across common or customer specific application components.
Recursive Questioning and Context Enhancement
SecurityReview.AI's Patent Pending and most innovative features is its recursive questioning methodology. The system generates follow-up queries based on initial document summaries, then uses these queries to extract additional relevant context from the vector databases. This iterative process ensures that threat models benefit from comprehensive contextual information rather than surface-level analysis. Using recursive questioning methodology, the system emulates the behaviour of an experienced security architect to derive the most refined outputs by way of threat scenarios & countermeasures relevant to the target application. This methodology ensures that AI hallucinations are practically eliminated, wherein the chance of it happening are close to zero.
Chain-of-thought prompting guides the AI agents through systematic analysis, breaking down threat identification into discrete steps: analyzing attack surfaces, assessing damage magnitude, evaluating user impact, and calculating severity scores. This structured approach ensures consistent, thorough analysis across different systems and applications.
The PWNISMS Framework:
Beyond Traditional Methodologies
While frameworks like STRIDE have served the security community well, they often prove inadequate for the complexity of modern, distributed applications. SecurityReview.AI introduces PWNISMS—a comprehensive threat modeling methodology that addresses seven critical security domains: Product, Workload, Network, Identity & Access Management (IAM), Secrets, Monitoring/Logging, and Supply Chain.

Product Security: Application-Level Threat Analysis
The Product component focuses on inherent security weaknesses within application architecture, design, and code. This includes analyzing data flows, trust boundaries, and critical use cases to uncover design flaws, logic vulnerabilities, insecure data handling, and improper error management that could lead to unauthorized data access or privilege escalation within the application.
Workload Security: Cloud-Native Infrastructure Protection
Workload assessment addresses the compute environment where modern applications predominantly reside—cloud infrastructure. This component examines containers, virtual machines, and serverless functions for misconfigurations such as open cloud storage or improper S3 bucket permissions. The analysis extends beyond basic configuration to examine the security posture of the entire compute workload.
Network Security: Communication and Segmentation Analysis
The Network component identifies threats related to inadequate network segmentation, open firewall ports, and insecure network protocols. It models scenarios including Man-in-the-Middle attacks, DNS poisoning, and lateral movement possibilities across network segments. This analysis proves particularly crucial for understanding how attackers might pivot through connected systems or exfiltrate data once inside the network perimeter.
Identity & Access Management: Authentication and Authorization Threats
IAM analysis addresses one of the most critical yet often undervalued aspects of application security. This component examines potential authentication and authorization abuses, including credential stuffing, brute force attacks, and privilege escalation scenarios. It also evaluates spoofing and impersonation risks while mapping threats to appropriate STRIDE categories for comprehensive coverage.
Secrets Management: Sensitive Data Protection
The Secrets component focuses on how applications and their environments handle sensitive information including passwords, API keys, encryption keys, certificates, and tokens. The analysis examines storage and transmission security, identifies potential secrets leakage scenarios, evaluates encryption adequacy, and assesses credential management practices to prevent attackers from gaining high-privilege access through compromised secrets.
Monitoring and Logging: Visibility and Audit Trail Security
Monitoring and Logging analysis examines the security of logging pipelines and audit systems. This component identifies risks from security log events that reveal excessive information, misconfigured logging systems, or missing audit logs that could hamper incident response and forensic analysis.
Supply Chain: Third-Party Risk Assessment
The Supply Chain component addresses threats from dependencies, including malicious components, compromised build processes, and vulnerabilities in third-party libraries or vendor-sourced components. This analysis proves increasingly critical as modern applications rely heavily on external dependencies and services.
Technical Architecture and Capabilities
Multi-Agent Processing Architecture
Multi-Agent Processing ArchitectureSecurityReview.AI employs specialized AI agents for each PWNISMS category, with dedicated agents for product threats, workload threats, network threats, and other security domains. Each agent receives specific prompting and instructions to specialize in its assigned threat generation category, ensuring depth and accuracy in analysis.
These agents interact with the system through multiple tools:
Knowledge Base Tool: Queries the Security Knowledge Database for relevant threat intelligence
Document Context Tool: Retrieves contextual information from project documentation
Document Context Tool: Retrieves contextual information from project documentation
Citations and Traceability
To address concerns about AI hallucination and ensure transparency, SecurityReview.AI provides comprehensive citations for every generated threat scenario and security objective. The system identifies specific document chunks and sources that informed each recommendation, enabling users to trace the reasoning behind every security finding.
Continuous Threat Modeling
SecurityReview.AI introduces Continuous Threat Modeling (CTM) capabilities that monitor connected data sources for changes and automatically trigger incremental threat modeling updates. When changes are detected, the system performs differential analysis, threat modeling only the modifications rather than re-analyzing entire systems. This approach enables iterative security analysis that keeps pace with rapid development cycles while minimizing resource consumption.
Advanced Code Analysis Capabilities
The platform includes sophisticated code repository analysis features that convert entire codebases into structured reports. Using advanced clustering algorithms, the system identifies important code sections and organizes them into logical chapters covering different functional areas such as logging, user management, and business logic. This automated code analysis provides comprehensive input for threat modeling without requiring manual code review.
Deployment and Integration Options
SecurityReview.AI recognizes the sensitive nature of threat modeling data and offers on-premises deployment options exclusively. Rather than providing a Software-as-a-Service model that might introduce data custody concerns, the platform deploys directly within customer cloud environments, ensuring complete data control and compliance with organizational security policies.
Multi-Cloud LLM Support
The platform supports multiple Large Language Model options to accommodate diverse organizational preferences and requirements.
OpenAI: Direct integration for organizations comfortable with OpenAI services
Azure OpenAI: For customers preferring Microsoft Azure cloud infrastructure
AWS Bedrock (Claude): For organizations using Amazon Web Services as their primary cloud platform
Container-Based Architecture
All deployments utilize container-based or Kubernetes-based architectures, ensuring consistent deployment across different cloud environments while maintaining scalability and management flexibility. This approach enables seamless integration with existing DevOps and container orchestration workflows.
Market Context and Competitive Advantage
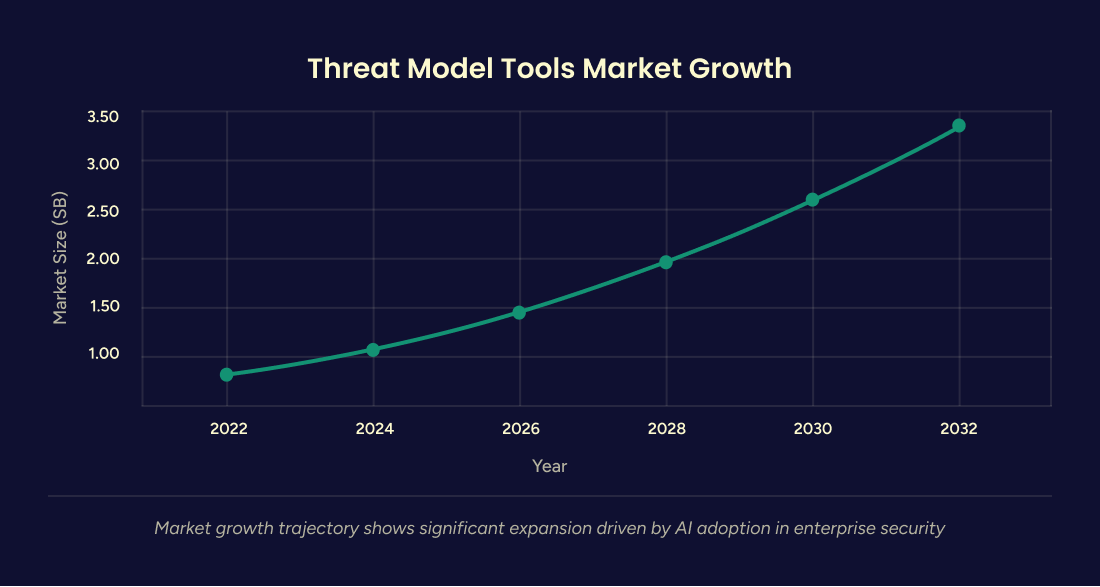
The threat modeling tools market demonstrates remarkable growth, valued at $886.6 million in 2022 and projected to reach $3.37 billion by 2032, representing a compound annual growth rate (CAGR) of 15.17%. This growth is driven by escalating cyber threats, increasing regulatory compliance requirements, and the rising adoption of AI-powered security solutions. AI adoption in security automation shows even more dramatic growth trajectories, with 81% of security leaders identifying automation as "very important" or "critically important" to their strategic plans over the next 3-5 years. Additionally, 27% of organizations expect AI to operate autonomously in key security areas, while 52% plan for AI to make complex decisions under human oversight.
Addressing Market Gaps
Traditional threat modeling tools suffer from significant limitations that SecurityReview.AI directly addresses:
Ease of Use: While many tools require extensive security expertise and have steep learning curves, SecurityReview.AI leverages natural language processing to make threat modeling accessible to development teams without deep security backgrounds.
Scalability: Conventional tools struggle with complex, distributed systems, whereas SecurityReview.AI's AI-native approach enables analysis of large-scale, cloud-native architectures without linear increases in resource requirements.
Integration: Most existing tools operate in isolation from development workflows, while SecurityReview.AI seamlessly integrates with existing tools and processes that development teams already use.
Consistency: Traditional manual approaches suffer from inconsistent outputs based on practitioner experience, whereas SecurityReview.AI's AI-driven analysis ensures consistent, comprehensive threat identification across different projects and teams.
The Future of AI-Native Security
SecurityReview.AI represents more than an evolution of traditional threat modeling—it embodies a fundamental transformation toward AI-native security practices that can keep pace with modern development velocities. By combining comprehensive threat analysis through the PWNISMS framework, advanced AI processing capabilities, and seamless integration with existing workflows, the platform addresses the core challenges that have long plagued enterprise threat modeling efforts.
The platform's vector database architecture and recursive questioning methodology ensure thorough analysis while maintaining the speed necessary for continuous security integration. Its multi-agent processing approach provides specialized expertise across different security domains while maintaining consistency and traceability through comprehensive citation capabilities.
As organizations increasingly adopt DevSecOps practices and seek to integrate security throughout their development lifecycles, solutions like SecurityReview.AI become essential for maintaining robust security postures without sacrificing development velocity. The platform's continuous threat modeling capabilities ensure that security analysis evolves alongside application development, providing dynamic protection that adapts to changing threat landscapes and system architectures.
The convergence of AI advancement and security imperative creates an unprecedented opportunity for organizations to transform their approach to threat modeling. SecurityReview.AI harnesses this convergence to deliver threat modeling that is faster, more comprehensive, and more consistent than traditional approaches while remaining deeply integrated with modern development practices. In an era where cyber threats evolve at machine speed, organizations require security solutions that operate at equivalent velocity—SecurityReview.AI provides exactly this capability through its AI-native architecture and comprehensive threat modeling framework. Through its innovative combination of AI processing, comprehensive integration capabilities, and specialized threat modeling methodology, SecurityReview.AI enables organizations to achieve the holy grail of modern security: comprehensive protection at development speed. This represents not just an improvement in threat modeling efficiency, but a fundamental transformation in how organizations can approach security architecture review in the age of cloud-native, AI-powered development.
